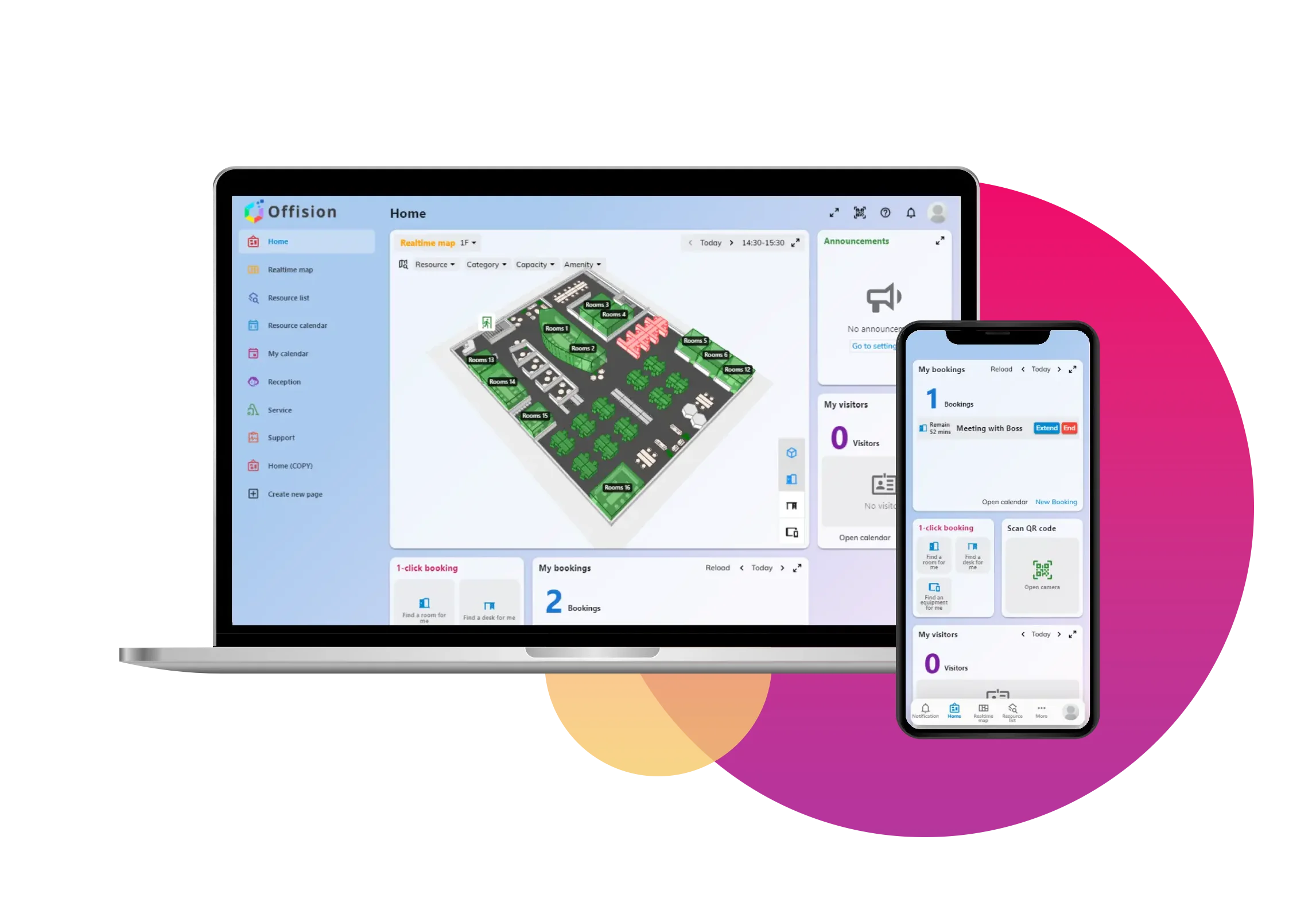
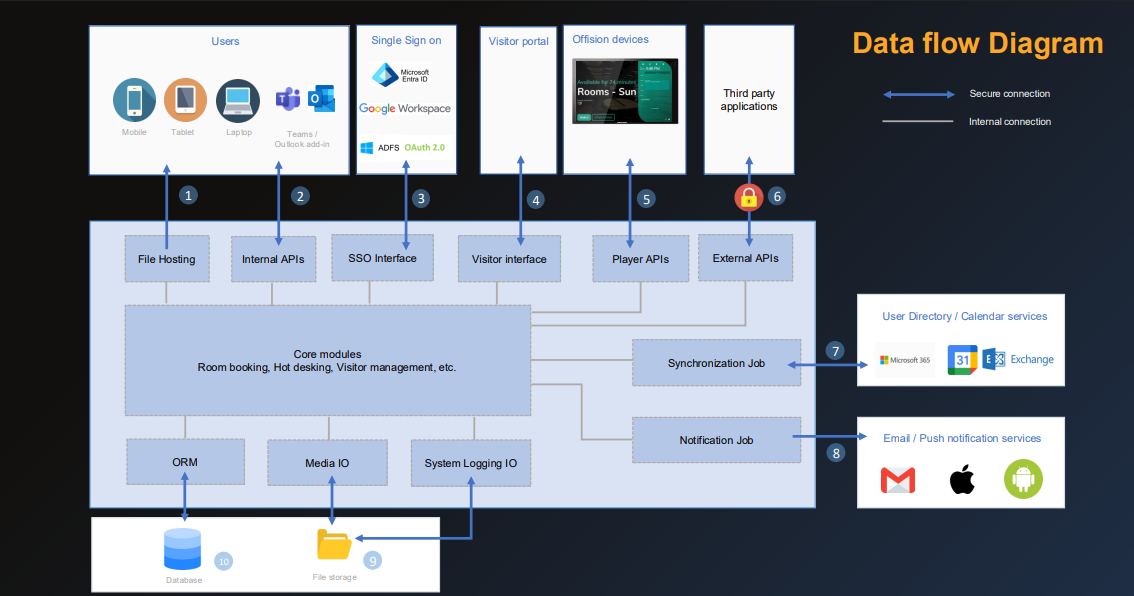
Company
Company
Select another country/region to browse the content applicable to your location.
Reminder
We have already sent a verification email to your mailbox. Please check your mailbox or junk mail folder. You can also click the resend button to send the verification email again.
Reminder
We have already sent a verification email to your mailbox. Please check your mailbox or junk mail folder. You can also contact us via hello@offision.com for further support.
Taiwan Agency Hotline
►PETACOM Technology Co., Ltd.
Tel: 02-2719-1128 - Ms. Huang(2380) & Ms. Lin(2382)
Email:
marketing@petacom.com.tw
Contact us
Submitting…
Email sent. We will contact you shortly.
Something is wrong! Please try again or contact via hello@offision.com.
Try Offision for free
More power. More productivity. Try our most-favourite features. Free for 1 month.